5 levels of ad-blocking

Ads are a necessary evil in some narratives. The narratives where the most talented techies & decision makers of the tech world created the ad delivery system. This system has reached the scale of such proportions that it now interacts with humanity as a whole in notorious ways. Look at this report which in the world of an unbiased 3rd party observer would read:
I am not going to start throwing information on how consolidation of massive amounts of personal data is a by product of massive ad delivery factories - and there are efforts to keep that in check going around the world notably by Apple & European Union.
All that geo-politics is really beyond me. I acknowledge the presence of the ad-monster & I really have very simple issues with it:
- ad-to-content ratio must be < 10% on static pages & 2% of time on dynamic sites. Unfortunately on instagram your mind is given a stimulus decided by the highest bidder every 3rd story.
- An analytics dashboard for the ad-viewers as good as the one for ad-creators - and ability to tweak ad-preferences with 100s of parameters to play with.
Keeping the battle b/w the systems aside; let's talk guerrilla warfare. Ads are evil & let us stop them grabbing our un-necessary attention because someone threw money to Mr. Zuck for adulterating 1B social feed's top posts - which happens everyday.
Level 1: The browser ad-blocker
There is nothing left to say about these. Already ~40% of the desktop users are aware of browser extensions or browsers themselves like firefox, brave, opera, vivaldi who based on their status in the food chain believe that ad-blocking comes in the required feature list of browsers. However, this does not cover mobile - where most of the mortal world plugs into the internet territory. These browsers are also offered on android & ios but they are powerless in other apps or webviews.
Level 2: The private DNS trick
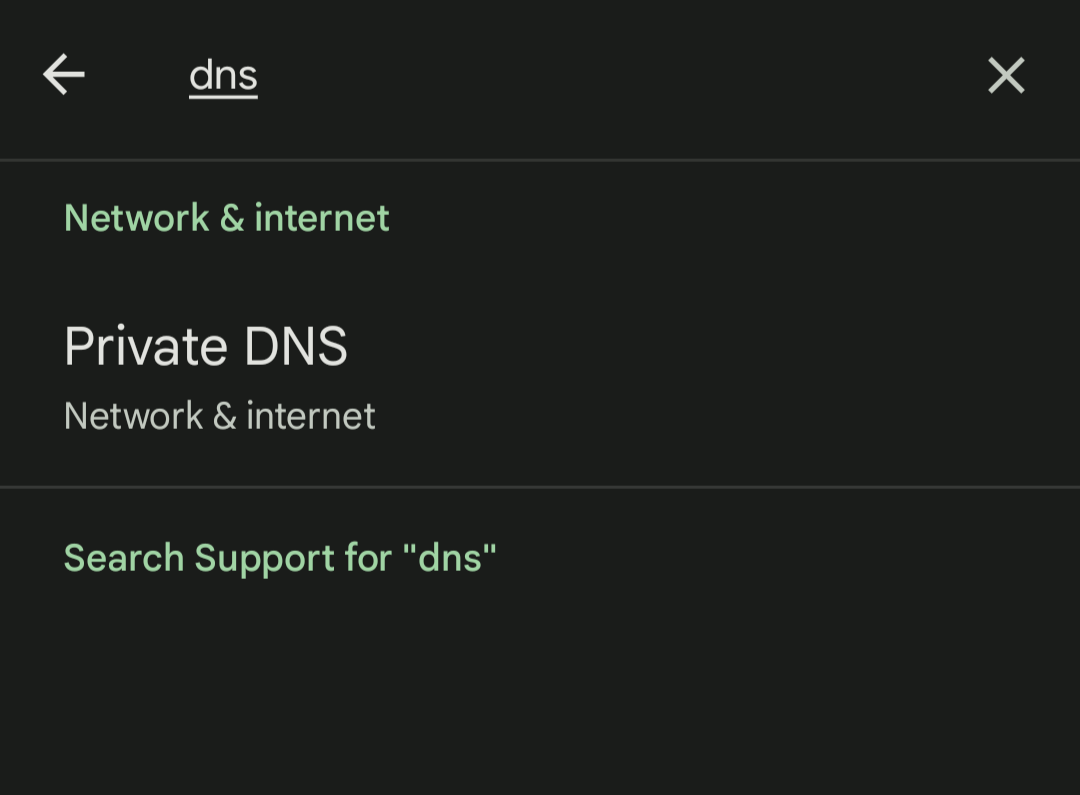
This is really an under appreciated feature in android! Just search for DNS in settings & enter: dns.adguard.com & browse to an ablock testing site to see your score immediately jump up!There are other public DNS providers with varying degrees/domains of blocking which one can choose from - here is one such list. For android, this works with mobile data - however, while another VPN is on - it can be flaky.
For iOS, the alternative option is to use an alternative DNS server's IP address in the wifi settings > manual DNS. Unfortunately will not work over mobile data.
Level 3: Buy adguard home
Technically this is level 4 if you don't mind spending 20$ on the premium version of the open source software mentioned in true level-4. The best option is to use their https-filtering approach by installing a CA certificate. In security perspective this is https-peeking is a standard in enterprise security these days by corporate VPNs. Additionally for adguard, the encryption keys of the certificates never leave your device.
So, it might feel like red-flags; but realistically speaking its designed to be safe unless in implementation there is a grand conspiracy b/w NSA & adguard.
Level 4: Host your own DNS
Okay, now things start getting uphill in complexity; however, the rewards are worth it. The basics:
Most ad-blockers (browser based or not) work majorly as a DNS filter. They change the answer about browser address (url) -> registered address of residence in internet's real-estate-registry. Instead of DNS filter, at this level, we shall setup our own DNS server!
Pre-requisite: This setup requires a linux server - physical or virtual.
- 👉🏼 Buy a router's sidekick: The recommended hardware is a raspberry pi - literally even the smallest pi zero works - which costs 5$ & <5W of electricity to be a little sidekick for your router. Install raspbian OR ubuntu by flashing the appropriate image.
- 👉🏼 Rent virtual-machine: If you want to go zero budget, get a linux VM (a really powerful one) for free in oracle cloud. This article will not go over the linux, network security list etc setup; the goal is to have a reasonably secure linux setup with port 53 open.
Steps: The docker way (recommended)
- Follow the instructions in this gist to setup adguard on your linux machine.
Steps: Without docker | source
# Run the following one-line automatic adguardhome installer
curl -s -S -L https://raw.githubusercontent.com/AdguardTeam/AdGuardHome/master/scripts/install.sh | sh -s -- -v
# Disclaimer: Do not expose adguard's admin ports on a machine on public cloud.Level 5: Create a secure home lab
If you have achieved level 3 or 4; I would say your defences against the ad-monster are top-of-the-line as of today. However, let's discuss; how we can take it a notch up! Let's see the issue with our setup at level-4:
❌ Does not work on mobile data network.
❌ If the DNS server is outside home (cloud), DNS port(s) needs to be open to the public internet.
Solution: We build on the setup from level-4 & create a private-p2p network for our devices & server. We shall use tailscale for this. The free tier is good enough to create a secure P2P network among 20 devices.

Steps: Reference
- Install tailscale on all your server(s), phones & laptops. This shall provide all your devices a permanent IP address which is only accessible over your tailscale devices
tailscale.com > DNS settings: Set the adguard home DNS server's IP.- Make sure no ports are exposed on servers.
- That's it! Now when you want to get rid of ads on your phone - just turn on tailscale application.
Level 5 is not an end goal - but the beginning of setting up of your private home lab.